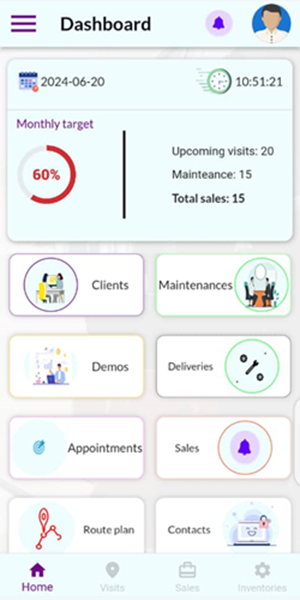
Valour CRM App
Welcome to Valour CRM, the ultimate mobile app designed to revolutionize your business operation across all industry sectors. like microfinance, insurance, product manufacturing and processing, transportation and logistics, retail, automotive, health care etc.
Quotation Module
The main purpose of this module is to generate and share quotations to clients once they express interest for a certain product/service
Clients module(Leads/Customers)
The main purpose of this module is to capture client details(any visited business). This data is important for mapping, keeping track of client details
Sales Module
This module will be able to facilitate in-app business sales and inventory management so that the user will be able to have basic sales information about the transactions made
Appointment Module
Efficiently schedule appointments with clients and ensure seamless calendar syncing and automation. The module sends reminders to sales personnel to keep them on track.
Features
Check The Features
Happy Clients
Projects
Hours Of Support
Hard Workers

Quotation Module.
Module Details :- The main purpose of this module is to generate and share quotations to clients once they express interest for a certain product/service. The quotation is generated by filling a form with the following field;
- Sending quotations to businesses.
- Monitoring customer interest(if they accepted/rejected).
- Update quotations.
Except for the above information, the quotation includes the business header(business information like business name, contacts, address, logo, etc).

Maintenance Module
Module Description :- The main purpose of this module is to help the business carry out periodic maintenance for the sold product. When a sale is made, the system will set a specific maintenance period e.g after 30 days, etc. a form with the following details is filled;
- Product(s) being maintained.
- Date of maintenance.
- Maintenance comment.
- Visit notes.

Demo Module
Module Description :- This module is important when a client requires to understand how the product they want to buy works. The business can schedule either an online meeting or to meet the client on the business places. A form with the following details is filled
- Demo date. The date on which the demo is done.
- Demo notes(what is the demo about?, what products are being demonstrated?, etc).
- Visit notes. Visit details.

Appointment Module
This module in the application is meant to collect data pertaining to meetings between the user and the prospect. It collects data on the following;
- Schedule appointments with clients. Syncing and automating with the calendar.
- Reminders for the sales personnel.
- Business information. This information will be related to details about the business such as; Business name, Contact information, Business location and Product categories etc.
- About meeting. This information will be related to the agenda and the purpose of the meeting, the date and the time when the meeting will be held between the user and the prospect.Time of the meeting(start and end time)
- Meeting notes. This data will be concerned with the purpose of the meeting and how it came to be.
Team
Our Great Team

Nkurunungi Gideon
Chief Executive Officer
Nuwagaba Eliab
Product Manager
Nsengiyumva wilberforce
Senior Dev
Ochwo David
Junior DevPricing
Check our Pricing
Free
$0 / month
- Aida dere
- Nec feugiat nisl
- Nulla at volutpat dola
- Pharetra massa
- Massa ultricies mi
Business
$19 / month
- Aida dere
- Nec feugiat nisl
- Nulla at volutpat dola
- Pharetra massa
- Massa ultricies mi
Developer
$29 / month
- Aida dere
- Nec feugiat nisl
- Nulla at volutpat dola
- Pharetra massa
- Massa ultricies mi
Ultimate
$49 / month
- Aida dere
- Nec feugiat nisl
- Nulla at volutpat dola
- Pharetra massa
- Massa ultricies mi
F.A.Q
Frequently Asked Questions
-
What tdo we mean by data? what do we mean by technology ?
We define data as information that needs to be processed, organised and structured for the sake of usability. In other words, by data we mean the information that you hold, such as details about the communities you work with, findings from research you have done, results from surveys, email addresses and contact information for supporters, and so on.
We understand technology as the tools, systems, methods and processes that capitalise on the computational power to manage, analyse and communicate information. For this resource, when we talk about technology, we mean digital tools, broadly. Anything from email platforms and messenger apps to website hosts, email newsletter platforms, CRMs, databases, algorithmic processes and more. -
What are the limits of AI in terms of development?
AI is a fascinating technology that can accomplish incredible tasks, but it also has its limits. Understanding these limitations is essential to having realistic expectations of what AI can accomplish.
First, AI relies heavily on data. It needs large amounts of data to learn and make decisions, which can be a challenge for companies that do not have access to large data sets. Another limitation is the lack of contextual understanding. If an AI is trained to perform a specific task, it can do so with great precision, but it can be lost in new or unpredictable situations. Moreover, AI is not creative and has no consciousness. She follows instructions and performs tasks based on these instructions, but she cannot think autonomously or feel emotions. Complex tasks that require deep understanding, such as solving complex problems or making ethical decisions, remain a challenge for AI. It has difficulty dealing with these issues satisfactorily. With respect to security and privacy, the use of AI in sensitive areas, such as medicine, raises data security and privacy concerns. Finally, AI is evolving rapidly, which means that AI professionals must constantly stay up to date to stay competent.
Understanding these limitations while exploring the possibilities of AI is essential to use this technology effectively and ethically. -
What is Social Engineering?
Social Engineering is the designation given to the set of persuasion techniques which purpose is getting users to execute or leverage actions in line with the attackers' goals.
Social engineering attacks are applicable in the context of cybersecurity as they can be applied in combination with attacks of technological nature. An example of this is the Phishing attack, in which a given user is induced to provide information or access to resources, under the illusion of being in contact with a trustworthy entity. -
How do i work with external developers and/or technologists?
There are many different types of external experts you can work with. Common types of external consultants/experts who interact with technology or data include:
User experience (UX) designer: Works with both clients (in this case, that’s you!) and users to design a product that satisfies multiple needs and is easy to understand and operate. Visual or Graphic Designer: Oversees the graphic elements that a website, tool, app or publication will use, and is responsible for designing the visual identity (or branding). They often work with the UX designer to make sure that the visual identity works well for users, too. Illustrator: Creates illustrations, icons, infographics and more, which will live within the larger structure that the Visual Designer and UX Designer have created. Frontend Developer: Implements the design on a website, tool or app. In particular, is able to code the aspects that users will see and interact with. Backend Developer: Develops and connects a database to the frontend (the parts of the website, app or tool that a user can see) and does all the non-visible tasks that will fill the frontend with dynamic content. Data Analyst/Scientist: Extracts patterns from large volumes of data. They may also be equipped with the tools and knowledge to create visualisations of data in order to communicate important patterns. Sysadmin/DevOps: Maintains the servers where the website, tool or app lives. They’re often responsible for coordinating the troubleshooting necessary if users encounter bugs or errors. Sometimes roles can overlap: for example, you could hire a consultant who leads the design and development of a website, or a developer who is capable of working on both the frontend and backend.
Before hiring external developers and technologists, it’s helpful to:
Be clear about why you want to build or adopt new tools. Identify the resources you have and those you will need. Remember to plan for long-term maintenance. At the beginning of your work together, it’s important to establish common ground and a shared terminology about needs and expectations. We recommend developing a ToR (Terms of Reference) in order to document and share project needs and requirements. The ToR should cover at minimum:
The available project budget The necessary timeline Your goals Your expectations for the external partner Any additional information You should also agree on tools, channels for communication, and roles and responsibilities.
All of this can greatly contribute to project success early on. Some “do’s” when working with consultants once the work is underway are:
Focus on clarity of organisational goals, big processes and milestones in order to better support the team/project. Provide relevant and timely feedback. Provide space and respect for the consultant’s expertise. Try to be responsive with communications. -
What is the expected evolution of Cybercrime?
It is expected that with the increasing use of information technologies that we have been observing, cybercrime will also follow this growing trend.
In addition to the growing pattern of cybercrime, it is also expected that attackers will become increasingly organised, structured and specialized, as it happens with traditional crime.
During the 90s and the 2000 decades, the preferred targets were the corporate, banking and insurance sectors. Currently, Cybercriminals have been diversifying their practices far beyond those target areas, and presently any entity or person can be a Cybercrime target.
Contact
Contact Us
Location:
Plot 40 Matyrs Way, Kampala
Opposite UNEB Uganda
Email:
info@impactoutsourcing.co.ug
Call:
+256752364557 / +256778766500